Best Three Pillars of Cyber security Digital Peace of Mind

The Three Pillers of Cyber security is non-negotiable, and with growing tech dependence, it must also gain complexity. Thus, we need to secure them from all kinds of malicious activities through physical and logical means so that individuals, organisations, and governments difference can differentiate the security zone by enabling comprehensive cybersecurity measures which will not only protect sensitive data systems against any cyber-attacks but also designed to provide house-to-house, Industrial network security with three essential elements: people, processes (conducts) and technology. The three elements constitute a valuable cybersecurity blueprint that will eliminate all possible threats.
Unique Securer’s Three Pillars of Cyber security solutions under the STARTech portfolio include Vulnerability Assessment, Risk Assessment, Incident Response, and Managed Security services. With an efficient, professional team of experts, you can only allow access to your business in the future. Our Custom Approach solutions are designed to fit your business-specific needs, so we cover each security aspect.
What is the significance of the Three Pillars of Cyber security?
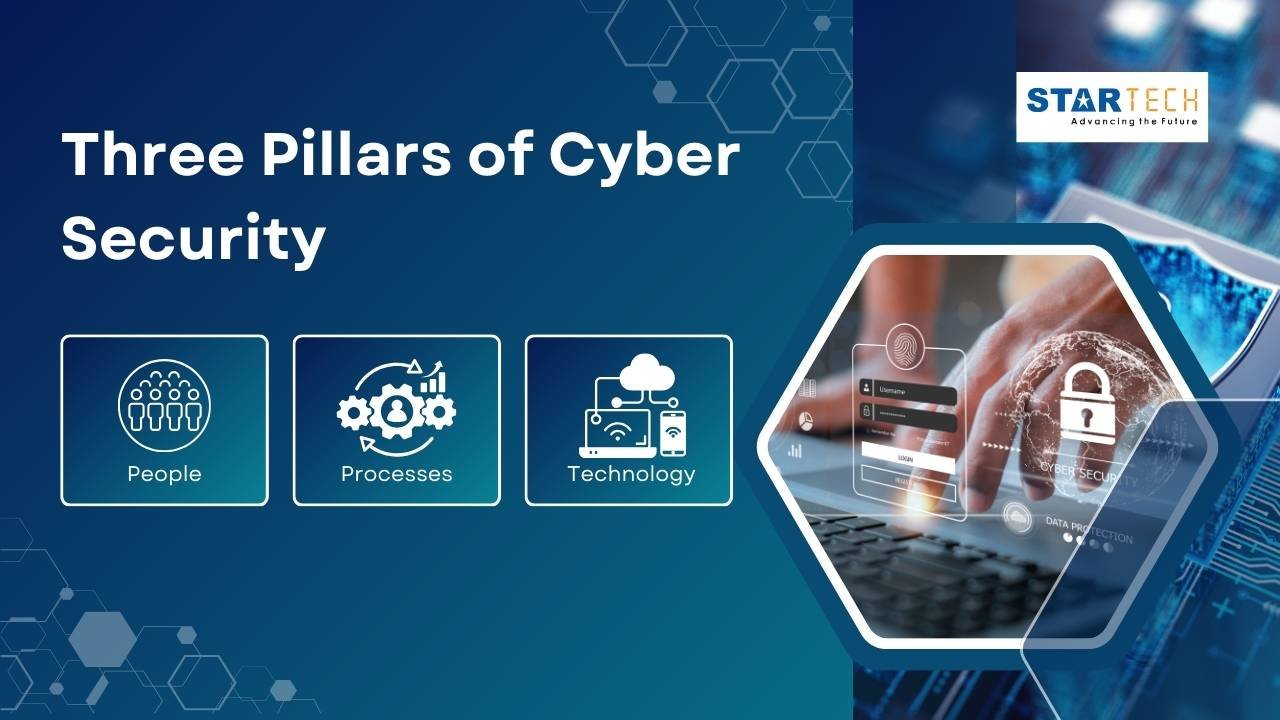
Three pillars of Cyber security comprise the fundamental elements of a complete security plan. They collaborate to safeguard individuals and organisations from cyberattacks.
1. People
Awareness of Security: employees are aware of all the cybersecurity threats and the best practices in avoiding becoming a victim of cyber-attacks by social engineering and making mistakes that compromise security. Education and Training: regularly scheduled education and training programs will help employees acquire the skills and abilities to develop recognition and to deal with the threat of potential attack. A good security culture will make an employee liable for specific actions and encourage him to report suspicious activities.
2. Processes
Policy and Procedure: The organisation needs to indicate policies and procedures that guide the employees to deal with sensitive information appropriately, ensure the safe use of technology, and respond appropriately when security incidents occur. Risk Management: Proper assessment must be enacted within organisations to address weaknesses and appropriately engage in mitigation efforts. Organisations need to have a plan of response towards any incident. A well-organised incident response plan can assist businesses in effectively dealing with security issues and recovering these.
3. Technology
Security Controls Implement appropriate security measures, like firewalls, intrusion detection system, or encryption systems, to safeguard the systems and data from unauthorised access. Up-to-date software and systems containing the latest security patches are some remedial steps to security faults. The continuous monitoring and logging of network activity may help detect and act against possible threats.
How to Harmonise the Three Core Pillars of Cybersecurity

Technology is essential to your business. It increases workers’ productivity, organises the company, and measures its financial health. Additionally, it provides effective communication methods. However, technology can only function when your workforce has been trained to use it.
Apart from these, your workforce requires processes to be in place for proper usage to prevent or curtail a data breach. It requires balancing among the three pillars of cybersecurity, and an information security plan helps overcome challenges.
1. Cybersecurity Challenges for All Organisations
Apart from these challenges, there are general cyber security challenges for all organisations, regardless of size or budget, since an organisation that needs a better defined or complete strategy needs more cohesive processes. Without such exploration, detection, and mitigation of cyber threats, the organisation would be unable to prevent cybercrimes. Technology cannot protect the organisation when people and processes are out of balance.
Fortune favours the business, for there are a sufficient number of choices to fight cyber challenges: the ever-changing threat panorama that challenges the balance amongst the three pillars and the appearance of AI and machine learning require innovation.
Cyber attackers already use new technologies to devise ways of committing new crimes. The task is to outpace them using the same technologies to develop better defences. For instance, a business might use machine learning algorithms to mine through vast data files to determine anomalies. Also, real-time discovery sets your business ahead by alerting it to the best possible defensive strategies before a breach occurs.
2. Cybersecurity Challenges for Large Corporations
Big organisations usually have the budget and human resources to maintain a security operation centre. With those resources, using and updating various security solutions to address different types of threats is very easy. However, the hefty security budget also comes with its set of problems.
First, the cost of labour will have to rise for the firm to sustain mass-scale network systems and processes. Second, the user means never-ending security alerts create what is loosely known as “alert fatigue” among IT security professionals whose time has better uses. If not dealt with, this will result in burnout and high turnover. Recruitment and replacement will be a burden on the remaining employees. This situation may expose the corporation to a cyberattack.
3. Small and Mid sized Companies Facing Cybersecurity Challenges
This business often only has limited funds dedicated to cybersecurity; thus, any SOC will likely prove too costly for most to implement and sustain. In addition, recruitment and retention of highly skilled IT professionals will also cost other departments and the bottom line. With these skills, there is a need for more cybersecurity. Without internal expertise, these businesses have turned into soft targets for cybercrimes. One hack into the database can break or shatter the company altogether.
IoT CyberSecurity Services and the Three Pillars

The Internet of Things has changed how we live in our world to such an extent that it now makes possible the connection of devices and systems in every field. Meanwhile, these interconnections have given rise to new cybersecurity problems. With this kind of unstable growth in IoT devices cybersecurity is all-important.
IoT Cybersecurity Services
- Security and Surveillance Assessment, Risk, and Scanning Assessing the vulnerability of IoT gadgets, networks, and software.
- Security audits and checks for compliance against standards and regulations in the industry and compliance checks against the most effective practices.
- Monitoring and Threat Intelligence: Monitor IoT intelligent systems for signs of active threat and collect details about new threats to study.
- Incident Response and Resolution: Develop solutions to respond to and resolve the security incident.
- Security awareness training informs employees and stakeholders of IoT-related risks and effective mitigation methods. A managed security service offers continuity by outsourcing cybersecurity functions to providers specialising in continuous protection.
What is continuous monitoring of cybersecurity? How is it beneficial?
Continuous cybersecurity monitoring is a form of cybersecurity surveillance that involves compelling an organisation to continually survey activities, system behaviours, and user activities meant to identify potential threats or vulnerabilities that might be exploited. It consists in collecting data from various sources, analysing and correlating the data in real-time, and accordingly carrying out this process with the aid of several tools and techniques that give the clients a snapshot of their security posture.
- Real-Time Threat Detection: Through continuous monitoring, organisations can detect cybersecurity threats as they emerge. Early identification of anomalies and breaches can help minimise cyberattacks such as ransomware attacks or data theft, which often have dire repercussions for business operations.
- Reduced Response Time: With real-time visibility, security teams can respond swiftly and decisively to incidents, mitigating risks before they cause irreparable harm. Faster response times help avoid downtime or security breaches that would delay security updates or breach protection measures for extended periods.
- Compliance and Audit: Many industries must abide by stringent regulations like GDPR, HIPAA, or PCI DSS, which must be observed regularly to remain compliant and reduce penalty risks. Monitoring helps keep systems compliant while streamlining audit processes and decreasing penalty risk.
- Increased Risk Management: Continuous system performance monitoring and security posture analysis give organisations vital insights into vulnerabilities, allowing them to prioritise risks and strengthen weak areas in their security infrastructure.
- Early Vulnerability Detection: Continuous monitoring can identify software vulnerabilities or misconfigurations before attackers exploit them, supporting proactive patch management and system hardening procedures to address weaknesses quickly and securely.
- Cost-effectiveness: Continuous monitoring can mitigate breaches or other security incidents, significantly lowering recovery costs, legal fees, and reputation damage.
- Improved System Resilience: By monitoring network activities closely, organisations can foster more resilient infrastructures that quickly adapt to emerging threats and challenges.
Conclusion
The Three Pillars of Cyber security(people, processes, and technology) and the balance between them are crucial in building a security posture. By taking care of all Three Pillars of Cyber security, organisations can effectively safeguard against cyber threats. In this modern era of the digitised world, with cyber-attacks looming right around the corner, having a well-built, secure Cyber Security base is indeed significant. Organisations can protect their valuable data, systems, and operations by ensuring security measures cover all bases.
FAQ
1. What are the three fundamental principles of cyber security?
Integrity, confidentiality, and accessibility should form the three cornerstones of an information security plan. Any plans created should adhere to at least one or all three.
2. What are the three P's of cyber security?
They usually consider the three pillars of cybersecurity processes, people, and products to strengthen security. One crucial factor that binds these two pillars is often overlooked—the necessity of providing comprehensive cybersecurity training teams.
3. What are the three main criteria for cybersecurity?
The security model’s importance speaks for itself: Confidentiality, integrity, and availability are infosec’s three most essential concepts. These three principles within the triad framework guide the development of security policies for organisations.
4. What is GRC Cyber Security?
Cyber security GRC encompasses governance, risk management, and compliance to enable an organisation to effectively oversee its IT strategy in line with business goals and regulatory obligations while meeting compliance needs.